Kioske Escape
Table of content
Configuration
It is possible to restrict the use of some binaries such as CMD.exe directly in the Windows configuration through the Prevent access to the command prompt policy available on User Configuration > Administrative Templates > System.
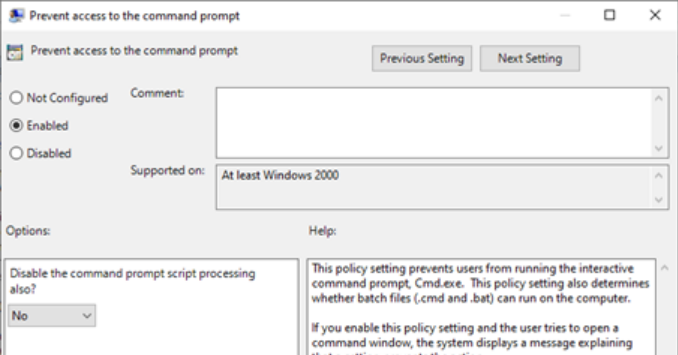
Likewise, it is possible to use registry keys:
HKLM\SOFTWARE\Policies\Microsoft\Windows\System\DisableCMD
HKCU\SOFTWARE\Policies\Microsoft\Windows\System\DisableCMD
These registry keys can have three values:
- 0 => Policy disabled
- 1 => Policy enabled and script processing disabled
- 2 => Policy enabled and script processing enabled
It is possible to bypass configuration 0 or 2. However, the bypass of 1 could be more challenging.
Powershell
Sometimes, the CMD is disabled but the PowerShell is not. It is then possible to directly use PowerShell : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Likewise, if PowerShell is blocked, try to use PowerShellISE : C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe.
In the case where AppLocker is securely configured, it is possible to bypass by copying the binary in another folder.
CMD /K /C
By using some CMD parameter, it is possible to bypass the restriction:
/k: Run the command specified and continue/c: Run the command and stop
Leveraging this parameter, it could be possible to run cmd.exe /k ${yourCommand} directly from the Windows Run (WIN+R) popup.
Autorun
The registry key SOFTWARE\Microsoft\Command Processor\AutoRun can be configured to launch a command when the CMD is ran without any parameter.
The HKLM key is run first and the HKCU is run after. By configuring your command in this registry key, it could be possible to bypass the restriction.
Shortcut
- Create a new shortcut
- Set your script as a target (
C:\Windows\System32\cmd.exe /k "whoami") - Open the shortcut
Batch file
Sometimes, the CMD is restricted but bat files can be run.
Thus, it is possible to emulate an interactive shell with the following bat script:
@echo off
:loop
set /p var=command:
%var%
goto loop
This bypass can be also used directly in the Windows RUN popup :
cmd.exe /q /v:on /k "FOR /L %N IN () DO (set /p var=command: && !var!)"
Word macro
The following VBA macro can be used to spawn a shell :
Sub Parent()
Set objWMIService = GetObject("winmgmts:{impersonationLevel=impersonate}!\\.\root\cimv2")
Set objStartup = objWMIService.Get("Win32_ProcessStartup")
Set objConfig = objStartup.SpawnInstance_
Set objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")
errReturn = objProcess.Create("C:\Windows\System32\cmd.exe", Null, objConfig, intProcessID)
End Sub
RunPE
If you have access to Office (WORD, EXCEL ...), it is possible to use process hollowing techniques to spawn a shell from a VBA macro: https://github.com/itm4n/VBA-RunPE