TrendMicro
Detections
Hooks
Hooks detections
Trendmicro seems to use several hooks to perform userland detection. The following hooks has been detected :
[+] 0x00007FF84DA00000 : ntdll.dll (C:\Windows\SYSTEM32\ntdll.dll)
[+] LdrLoadDll
[+] LdrUnloadDll
[+] NtCreateMutant
[+] NtCreateThread
[+] NtCreateThreadEx
[+] NtDeviceIoControlFile
[+] NtDuplicateToken
[+] NtLoadDriver
[+] NtMapViewOfSection
[+] NtProtectVirtualMemory
[+] NtQueueApcThread
[+] NtReadVirtualMemory
[+] NtSetContextThread
[+] NtSetInformationThread
[+] NtTerminateProcess
[+] NtWriteVirtualMemory
[+] 0x00007FF84D670000 : KERNEL32.DLL (C:\Windows\System32\KERNEL32.DLL)
[+] CopyFileA
[+] CopyFileExA
[+] CreateRemoteThread
[+] CreateToolhelp32Snapshot
[+] MoveFileA
[+] MoveFileExA
[+] MoveFileW
[+] MoveFileWithProgressA
[+] 0x00007FF84A620000 : KERNELBASE.dll (C:\Windows\System32\KERNELBASE.dll)
[+] CopyFileExW
[+] CopyFileW
[+] CreateProcessInternalA
[+] CreateProcessInternalW
[+] CreateRemoteThreadEx
[+] ImpersonateLoggedOnUser
[+] MoveFileExW
[+] MoveFileWithProgressW
[+] VirtualAlloc
[+] VirtualAllocEx
[+] WriteProcessMemory
[+] 0x00007FF84D860000 : ADVAPI32.dll (C:\Windows\System32\ADVAPI32.dll)
[+] CreateProcessWithTokenW
[+] CreateRestrictedToken
[+] CreateServiceA
[+] CreateServiceW
[+] EncryptFileW
The WriteProcessMemory and NtWriteVirtualMemory trigger an hard detection.
The VirtualAlloc, VirtualAllocEx, CreateToolhelp32Snapshot and LdrLoadDll does not seem to trigger any detection.
During process creation, the following DLL are loaded in the process by TrendMicro:
C:\Windows\system32\tmumh\20019\AddOn\8.55.0.1257\TmUmEvt64.dll
C:\Windows\system32\tmumh\20019\TmMon\2.9.0.1052\tmmon64.dll
C:\Windows\System32\TmLWE\TmUmSnsr64\1.0.0.1121\TmUmSnsr64.dll
NtWriteVirtualMemory
For this function, the hook is located in the tmmon64.dll DLL file at the 0x21664 offset.
However, looking at this address in the DLL with IDA shows an empty function:
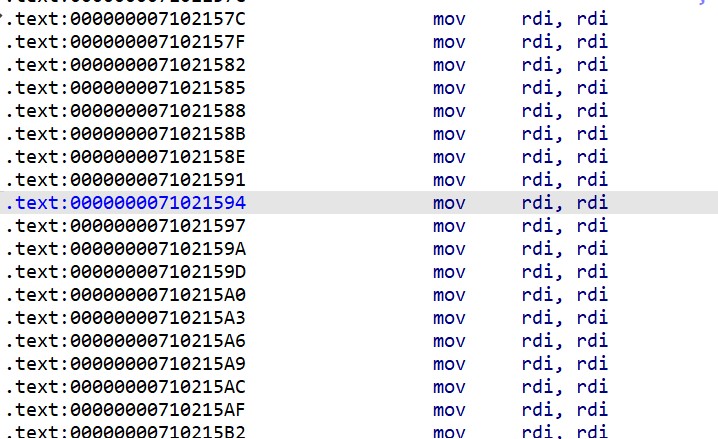
The function must be dynamically initialized. So let's directly debug it in IDA with a process debugged.
Unhooking
It is possible to easily bypass userland hook detection using the HardwareBreakpoint technique.
ETW
TrendMicro use specific ETW tracing sessions:
TMSYSEVT_ETW
TmOwl-{1C95126E-7EEA-49A9-A3FE-A378B03DDB4D}+Microsoft-Windows-DNS-Client Trace
TmOwl-{2F07E2EE-15DB-40F1-90EF-9D7BA282188A}+Microsoft-Windows-TCPIP Trace
TmOwl-{1418EF04-B0B4-4623-BF7E-D74AB47BBDAA}+Microsoft-Windows-WMI-Activity Trace
TmOwl-{DE7B24EA-73C8-4A09-985D-5BDADCFA9017}+Microsoft-Windows-TaskScheduler Trace
TmOwl-{43D1A55C-76D6-4F7E-995C-64C711E5CAFE}+Microsoft-Windows-WinINet Trace
It seems that it is possible to deactivate the ETW tracing session with the following command:
logman stop TMSYSEVT_ETW -ets
It is possible to do it programatically with the following C code line:
ULONG status = StopTraceW((TRACEHANDLE)NULL, L"TMSYSEVT_ETW", procmonTracingSession);
Drivers
TrendMicro use the tbimdsa.sys driver.
It seems that the driver is using Windows Filter Driver capabilities:
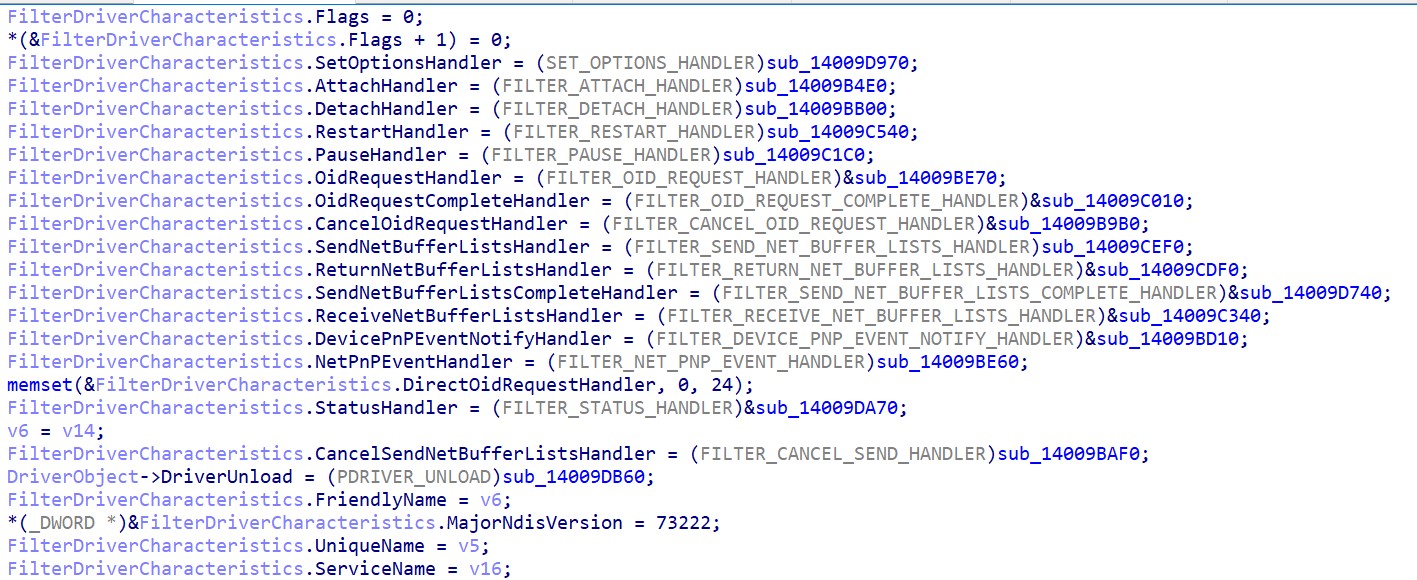
The filter is registered with the GUID {8A16B9CA-6C16-486e-8E32-DEBBBC5E8090} and the friendly name Trend Micro NDIS 6.0 Filter driver.
Cloud console
Endpoint alerts
https://portal.eu.xdr.trendmicro.com/index.html#/app/threat-hunting